先看效果
kubectl apply -f deploy.yaml
执行上面的命令后,通过netstat -nltp 确认本机80、443是nginx进程在监听
apiVersion: v1kind: Namespacemetadata:name: ingress-nginxlabels:: ingress-nginx: ingress-nginx---# Source: ingress-nginx/templates/controller-serviceaccount.yamlapiVersion: v1kind: ServiceAccountmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginxnamespace: ingress-nginx---# Source: ingress-nginx/templates/controller-configmap.yamlapiVersion: v1kind: ConfigMapmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginx-controllernamespace: ingress-nginxdata:---# Source: ingress-nginx/templates/clusterrole.yamlapiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helmname: ingress-nginxnamespace: ingress-nginxrules:apiGroups:''resources:configmapsendpointsnodespodssecretsverbs:listwatchapiGroups:''resources:nodesverbs:getapiGroups:''resources:servicesverbs:getlistupdatewatchapiGroups:extensionsnetworking.k8s.io # k8s 1.14+resources:ingressesverbs:getlistwatchapiGroups:''resources:eventsverbs:createpatchapiGroups:extensionsnetworking.k8s.io # k8s 1.14+resources:ingresses/statusverbs:updateapiGroups:networking.k8s.io # k8s 1.14+resources:ingressclassesverbs:getlistwatch---# Source: ingress-nginx/templates/clusterrolebinding.yamlapiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helmname: ingress-nginxnamespace: ingress-nginxroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: ingress-nginxsubjects:kind: ServiceAccountname: ingress-nginxnamespace: ingress-nginx---# Source: ingress-nginx/templates/controller-role.yamlapiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginxnamespace: ingress-nginxrules:apiGroups:''resources:namespacesverbs:getapiGroups:''resources:configmapspodssecretsendpointsverbs:getlistwatchapiGroups:''resources:servicesverbs:getlistupdatewatchapiGroups:extensionsnetworking.k8s.io # k8s 1.14+resources:ingressesverbs:getlistwatchapiGroups:extensionsnetworking.k8s.io # k8s 1.14+resources:ingresses/statusverbs:updateapiGroups:networking.k8s.io # k8s 1.14+resources:ingressclassesverbs:getlistwatchapiGroups:''resources:configmapsresourceNames:ingress-controller-leader-nginxverbs:getupdateapiGroups:''resources:configmapsverbs:createapiGroups:''resources:endpointsverbs:creategetupdateapiGroups:''resources:eventsverbs:createpatch---# Source: ingress-nginx/templates/controller-rolebinding.yamlapiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginxnamespace: ingress-nginxroleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: ingress-nginxsubjects:kind: ServiceAccountname: ingress-nginxnamespace: ingress-nginx---# Source: ingress-nginx/templates/controller-service-webhook.yamlapiVersion: v1kind: Servicemetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginx-controller-admissionnamespace: ingress-nginxspec:type: ClusterIPports:name: https-webhookport: 443targetPort: webhookselector:: ingress-nginx: ingress-nginx: controller---# Source: ingress-nginx/templates/controller-service.yamlapiVersion: v1kind: Servicemetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginx-controllernamespace: ingress-nginxspec:type: LoadBalancerexternalTrafficPolicy: Localports:name: httpport: 80protocol: TCPtargetPort: httpname: httpsport: 443protocol: TCPtargetPort: httpsselector:: ingress-nginx: ingress-nginx: controller---# Source: ingress-nginx/templates/controller-deployment.yamlapiVersion: apps/v1kind: Deploymentmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: controllername: ingress-nginx-controllernamespace: ingress-nginxspec:selector:matchLabels:: ingress-nginx: ingress-nginx: controllerrevisionHistoryLimit: 10minReadySeconds: 0template:metadata:labels:: ingress-nginx: ingress-nginx: controllerspec:dnsPolicy: ClusterFirsthostNetwork: truenodeSelector:app: ingresscontainers:name: controllerimage: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.32.0imagePullPolicy: IfNotPresentlifecycle:preStop:exec:command:/wait-shutdownargs:/nginx-ingress-controller--publish-service=ingress-nginx/ingress-nginx-controller--election-id=ingress-controller-leader--ingress-class=nginx--configmap=ingress-nginx/ingress-nginx-controller--validating-webhook=:8443--validating-webhook-certificate=/usr/local/certificates/cert--validating-webhook-key=/usr/local/certificates/keysecurityContext:capabilities:drop:ALLadd:NET_BIND_SERVICErunAsUser: 101allowPrivilegeEscalation: trueenv:name: POD_NAMEvalueFrom:fieldRef:fieldPath: metadata.namename: POD_NAMESPACEvalueFrom:fieldRef:fieldPath: metadata.namespacelivenessProbe:httpGet:path: /healthzport: 10254scheme: HTTPinitialDelaySeconds: 10periodSeconds: 10timeoutSeconds: 1successThreshold: 1failureThreshold: 3readinessProbe:httpGet:path: /healthzport: 10254scheme: HTTPinitialDelaySeconds: 10periodSeconds: 10timeoutSeconds: 1successThreshold: 1failureThreshold: 3ports:name: httpcontainerPort: 80protocol: TCPname: httpscontainerPort: 443protocol: TCPname: webhookcontainerPort: 8443protocol: TCPvolumeMounts:name: webhook-certmountPath: /usr/local/certificates/readOnly: trueresources:requests:cpu: 100mmemory: 90MiserviceAccountName: ingress-nginxterminationGracePeriodSeconds: 300volumes:name: webhook-certsecret:secretName: ingress-nginx-admission---# Source: ingress-nginx/templates/admission-webhooks/validating-webhook.yamlapiVersion: admissionregistration.k8s.io/v1beta1kind: ValidatingWebhookConfigurationmetadata:labels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhookname: ingress-nginx-admissionnamespace: ingress-nginxwebhooks:name: validate.nginx.ingress.kubernetes.iorules:apiGroups:extensionsnetworking.k8s.ioapiVersions:v1beta1operations:CREATEUPDATEresources:ingressesfailurePolicy: FailclientConfig:service:namespace: ingress-nginxname: ingress-nginx-controller-admissionpath: /extensions/v1beta1/ingresses---# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrole.yamlapiVersion: rbac.authorization.k8s.io/v1kind: ClusterRolemetadata:name: ingress-nginx-admissionannotations:: pre-install,pre-upgrade,post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxrules:apiGroups:admissionregistration.k8s.ioresources:validatingwebhookconfigurationsverbs:getupdate---# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrolebinding.yamlapiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata:name: ingress-nginx-admissionannotations:: pre-install,pre-upgrade,post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: ingress-nginx-admissionsubjects:kind: ServiceAccountname: ingress-nginx-admissionnamespace: ingress-nginx---# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-createSecret.yamlapiVersion: batch/v1kind: Jobmetadata:name: ingress-nginx-admission-createannotations:: pre-install,pre-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxspec:template:metadata:name: ingress-nginx-admission-createlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhookspec:containers:name: createimage: jettech/kube-webhook-certgen:v1.2.0imagePullPolicy: IfNotPresentargs:create--host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.ingress-nginx.svc--namespace=ingress-nginx--secret-name=ingress-nginx-admissionrestartPolicy: OnFailureserviceAccountName: ingress-nginx-admissionsecurityContext:runAsNonRoot: truerunAsUser: 2000---# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-patchWebhook.yamlapiVersion: batch/v1kind: Jobmetadata:name: ingress-nginx-admission-patchannotations:: post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxspec:template:metadata:name: ingress-nginx-admission-patchlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhookspec:containers:name: patchimage: jettech/kube-webhook-certgen:v1.2.0imagePullPolicy:args:patch--webhook-name=ingress-nginx-admission--namespace=ingress-nginx--patch-mutating=false--secret-name=ingress-nginx-admission--patch-failure-policy=FailrestartPolicy: OnFailureserviceAccountName: ingress-nginx-admissionsecurityContext:runAsNonRoot: truerunAsUser: 2000---# Source: ingress-nginx/templates/admission-webhooks/job-patch/role.yamlapiVersion: rbac.authorization.k8s.io/v1kind: Rolemetadata:name: ingress-nginx-admissionannotations:: pre-install,pre-upgrade,post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxrules:apiGroups:''resources:secretsverbs:getcreate---# Source: ingress-nginx/templates/admission-webhooks/job-patch/rolebinding.yamlapiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata:name: ingress-nginx-admissionannotations:: pre-install,pre-upgrade,post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginxroleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: ingress-nginx-admissionsubjects:kind: ServiceAccountname: ingress-nginx-admissionnamespace: ingress-nginx---# Source: ingress-nginx/templates/admission-webhooks/job-patch/serviceaccount.yamlapiVersion: v1kind: ServiceAccountmetadata:name: ingress-nginx-admissionannotations:: pre-install,pre-upgrade,post-install,post-upgrade: before-hook-creation,hook-succeededlabels:: ingress-nginx-2.0.3: ingress-nginx: ingress-nginx: 0.32.0: Helm: admission-webhooknamespace: ingress-nginx
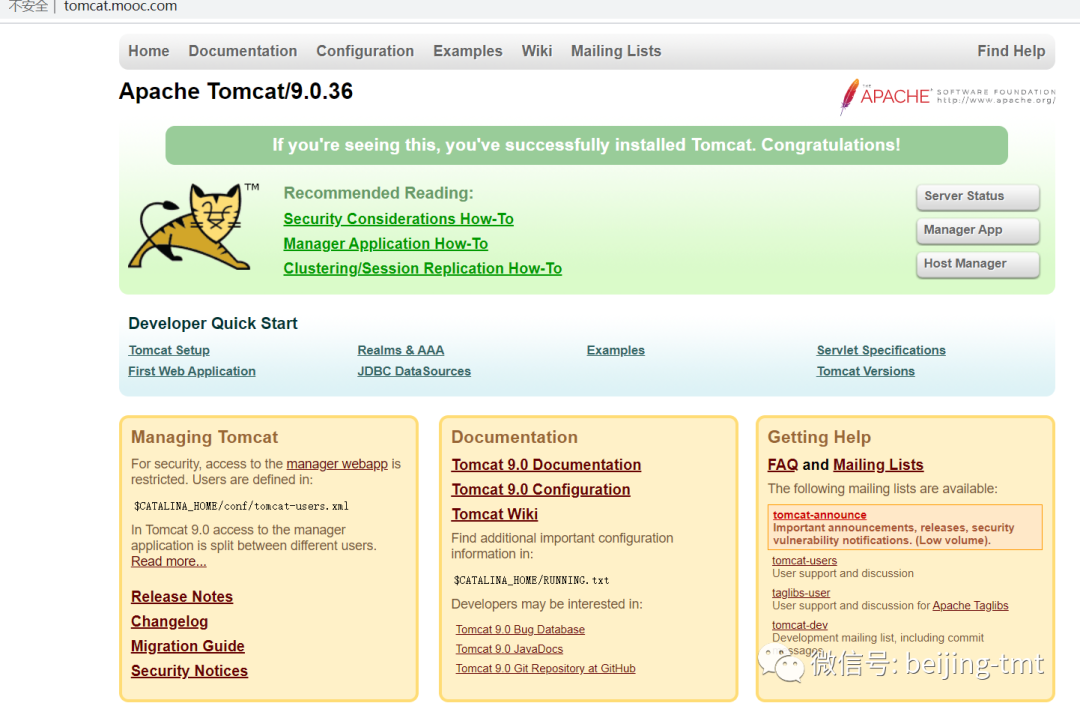
tomcat-demo.yaml
执行kubectl apply -f tomcat-demo.yaml
(注意我, 这个是arm64实现成功。如果不是arm的系统,可以换成amd64的image)
apiVersion: apps/v1kind: Deploymentmetadata:name: tomcat-demospec:selector:matchLabels:app: tomcat-demoreplicas: 1template:metadata:labels:app: tomcat-demospec:containers:name: tomcat-demoimage: arm64v8/tomcat:9.0ports:containerPort: 8080---#serviceapiVersion: v1kind: Servicemetadata:name: tomcat-demospec:ports:port: 80protocol: TCPtargetPort: 8080selector:app: tomcat-demo---#ingressapiVersion: extensions/v1beta1kind: Ingressmetadata:name: tomcat-demospec:rules:host: tomcat.mooc.comhttp:paths:path: /backend:serviceName: tomcat-demoservicePort: 80#有需要交流的,可以添加作者微信419644560#备注:k3s
本文分享自微信公众号 - 架构师智库(beijing-tmt)。
如有侵权,请联系 support@oschina.cn 删除。
本文参与“OSC源创计划”,欢迎正在阅读的你也加入,一起分享。
来源:oschina
链接:https://my.oschina.net/u/4585832/blog/4405585